A Python NIDS that captures live traffic from the active network interface, identifies suspicious behaviour (risky services, port scans, uncommon protocols, high packet rates), and emits actionable alerts in real time. The output mirrors SOC workflows with concise [ALERT]/[INFO] lines that analysts can paste directly into tickets.
AsyncSniffer).
The goal was to capture packets live from a chosen interface, apply both signature-based and anomaly-based checks, and continuously surface alerts for quick triage. The design favours low complexity and high explainability so detections are easy to validate.
AsyncSniffer for live captureAsyncSniffer with a per-packet callback to parse headers.# Linux / macOS (root needed to sniff)
sudo python3 main.py
# Output example:
# [*] Sniffer started on eth1 - press Ctrl+C to stop.
# [ALERT] Suspicious TCP port detected: 3389 (RDP) from 192.168.56.102 to 192.168.56.101
# ...
Use a second VM/host to generate traffic (nc, nmap, ping) and watch the alerts stream in.
Detect access to sensitive/abused services (RDP/3389, NTP/123, etc.).

exampleattack1-tcp.png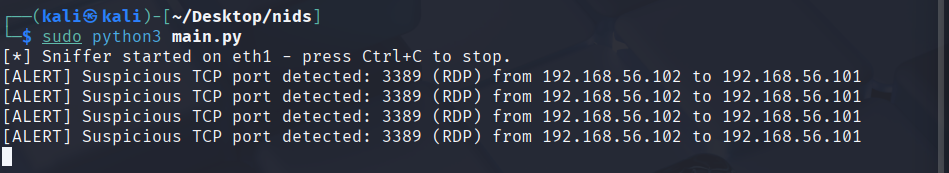
exampleoutput1-tcp.png
exampleattack1-udp.png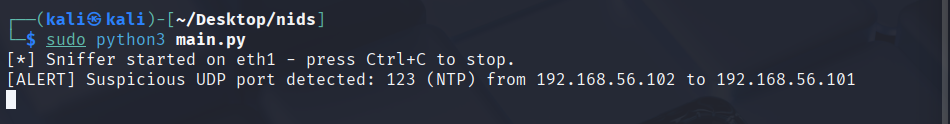
exampleoutput1-udp.pngDetect ≥10 unique destination ports to the same host within ~5s.
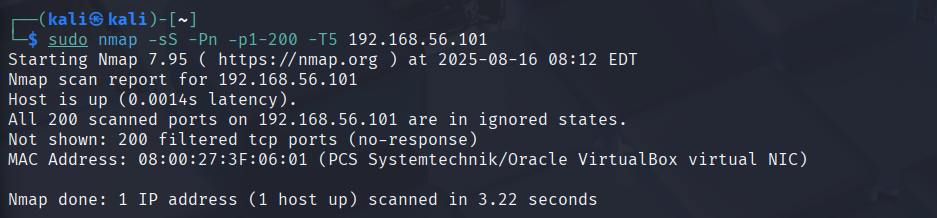
exampleattack2.png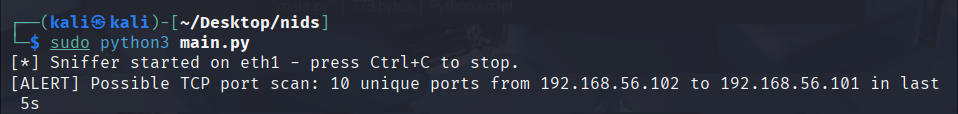
exampleoutput2.pngFlag when a source sends ≥100 packets in a 10s window.
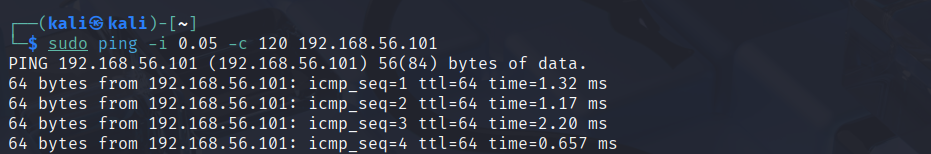
exampleattack3.png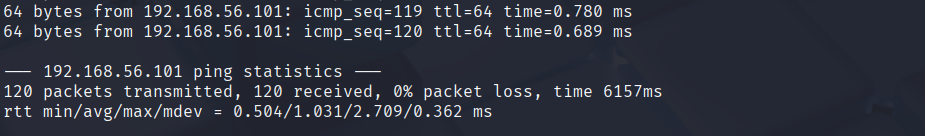
exampleattack3.1.png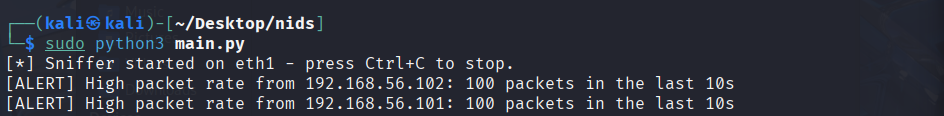
exampleoutput3.pngFlag traffic using uncommon IP protocols (e.g., GRE/47).

exampleattack4.png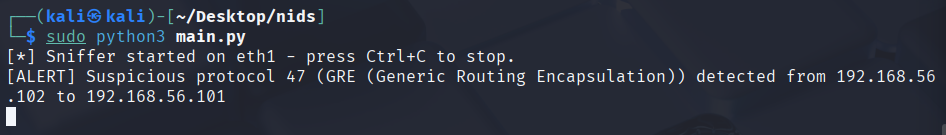
exampleoutput4.png