A lightweight Python pipeline that parses SIEM-style JSONL logs, runs rule-based and statistical anomaly checks, and emits readable alerts with timestamps, actors, windows, and thresholds — ready for SOC triage.
event_type.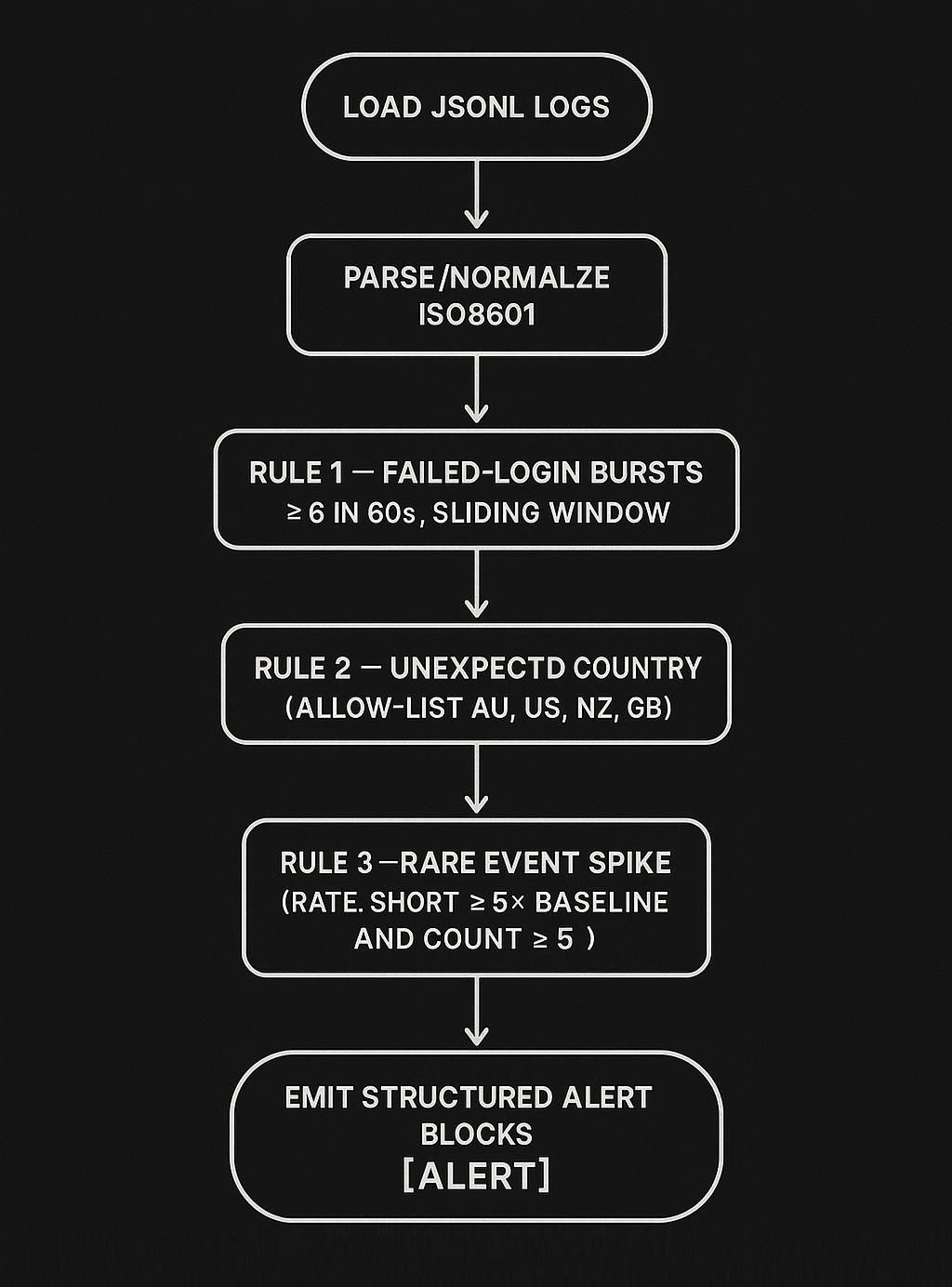
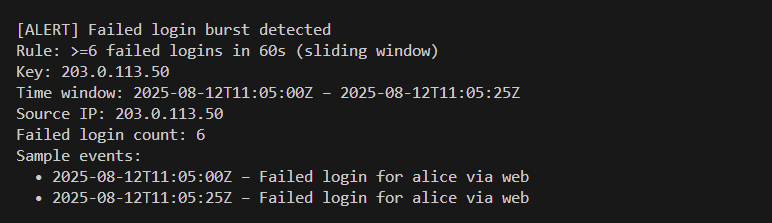
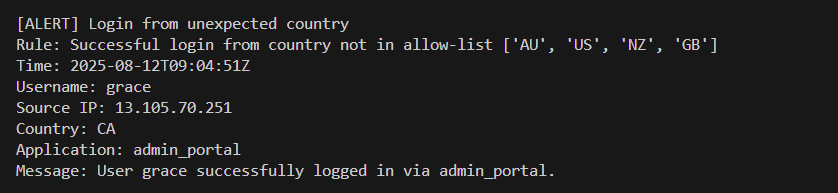
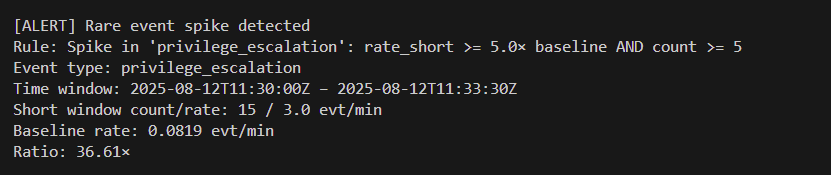
The brief: parse SIEM logs, detect anomalies (failed-login bursts, unusual countries, rare events), and produce clear alerts/reporting. I focused on fast sliding windows and copy-pasteable messages that match real SOC hand-offs.
datetime, collections.deque, defaultdict)fails ≥ 6 within 60s. Include actor + sample events and apply cooldown to reduce noise.country ∉ allowlist (defaults: AU, US, NZ, GB). Includes username, app, source IP.event_type, compute short-window rate vs baseline; alert when rate_short ≥ 5× baseline and count ≥ 5.{ ts, event_type, outcome, username, src_ip, country, app, msg } (fields vary per line).# From project root
python main.py
# The tool parses 'siem_sample_logs.jsonl' and prints alerts it detects.